Have you ever noticed login attempts through ssh that are not any of your users?
I deployed a server on Digital Ocean about a week ago and, almost immediately, I started getting these login attempts.
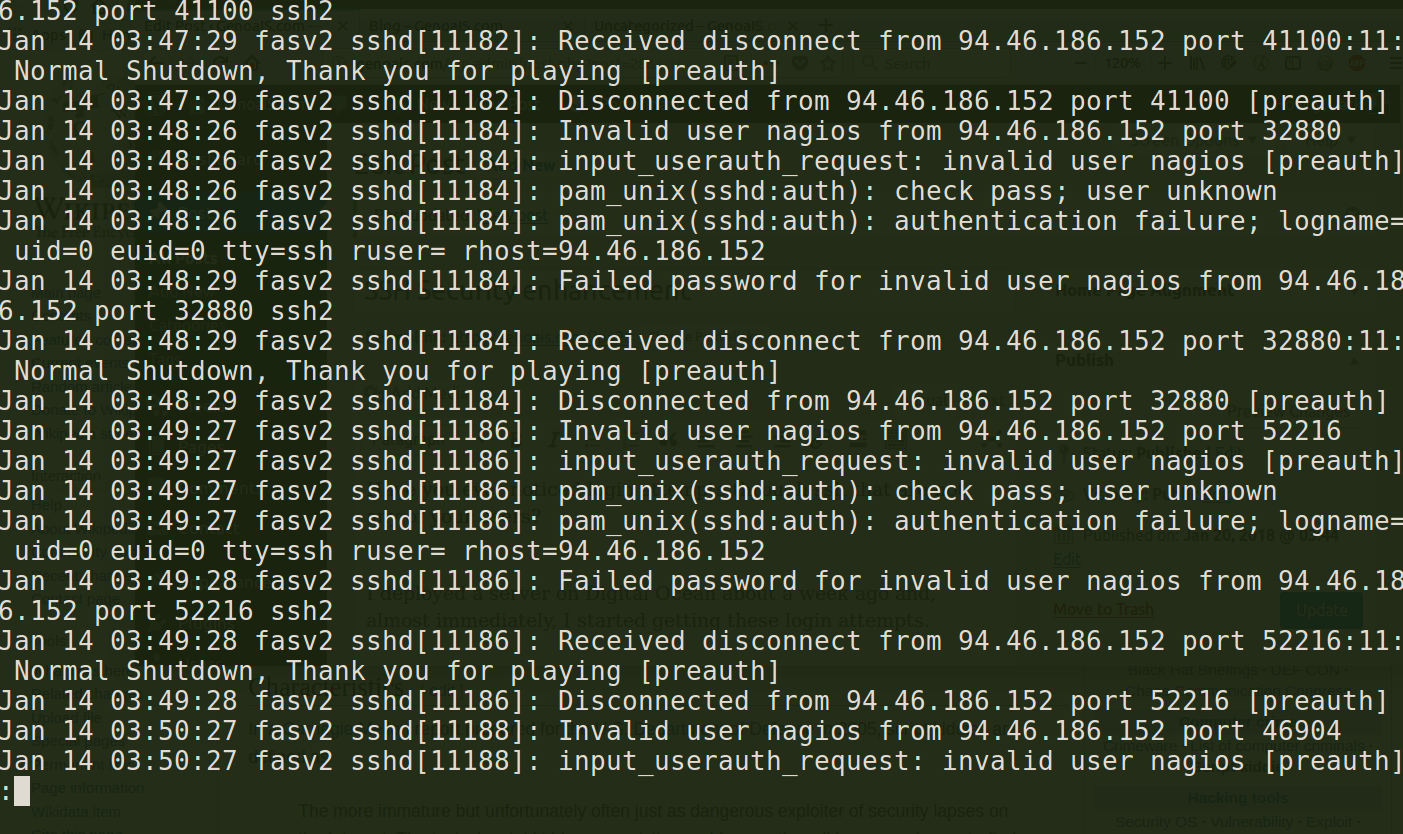
Look at this snippet from the log file. Login attempts from user nagios, postgres, deploy and others. I'm not running Nagios or PostgreSQL. I don't have a user deploy. I'm very careful to use different names to prevent an inadvertent hole in the system.
Jan 14 03:59:56 fasv2 sshd[11212]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=94.46.186.152 user=postgres Jan 14 03:59:56 fasv2 sshd[11212]: pam_succeed_if(sshd:auth): requirement "uid >= 1000" not met by user "postgres" Jan 14 03:59:59 fasv2 sshd[11212]: Failed password for postgres from 94.46.186.152 port 35512 ssh2 Jan 14 03:59:59 fasv2 sshd[11212]: Received disconnect from 94.46.186.152 port 35512:11: Normal Shutdown, Thank you for playing [preauth] Jan 14 03:59:59 fasv2 sshd[11212]: Disconnected from 94.46.186.152 port 35512 [preauth] Jan 14 04:00:58 fasv2 sshd[11216]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=94.46.186.152 user=postgres Jan 14 04:00:58 fasv2 sshd[11216]: pam_succeed_if(sshd:auth): requirement "uid >= 1000" not met by user "postgres" Jan 14 04:00:59 fasv2 sshd[11216]: Failed password for postgres from 94.46.186.152 port 57054 ssh2 Jan 14 04:01:00 fasv2 sshd[11216]: Received disconnect from 94.46.186.152 port 57054:11: Normal Shutdown, Thank you for playing [preauth] Jan 14 04:01:00 fasv2 sshd[11216]: Disconnected from 94.46.186.152 port 57054 [preauth] Jan 14 04:01:59 fasv2 sshd[11232]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=94.46.186.152 user=postgres Jan 14 04:01:59 fasv2 sshd[11232]: pam_succeed_if(sshd:auth): requirement "uid >= 1000" not met by user "postgres" Jan 14 04:02:01 fasv2 sshd[11232]: Failed password for postgres from 94.46.186.152 port 50320 ssh2
Notice the amount of log entries they created. The number of attempts can be overwhelming over time. In my experience, the number of users/systems that try to log into your server will increase. I guess as time goes by and your system gets more exposure through DNS, your system becomes more attractive. Think of a DNS entry as an invitation to bad guys.
Whether they're script kiddies or serious hackers, I don't know. Regardless, I don't want to worry about these incidents or waste computer cycles processing them.
A super simple solution that will eliminate these login attempts and enhance security for your server is to change the port that SSH listens to.
To do that, edit /etc/ssh/sshd_config And make the following changes:
#Port 22
Port 39999
Make sure that port 22 is commented out. Add a new line with Port and the number of the port. I use a number that I can remember. It's easy to remember. Since port 22 is a published standard, it's always tested. Like a thief jiggling the handle on a door to see if it's unlocked. You can avoid all the riff raff coming your way by changing it to a non-standard number. Just remember to adjust your firewall and router to allow connections coming into that port.
If your're behind a firewall or a router, you can have the router or firewall accept connections on port 39999 and forward it to port 22 on your server.
I know there are many ways of enhancing security, this is one of the most simple ways to do it.